Cisco Certified Network Associate (CCNA), a certification which is the basic or the fundamental one in Network Career. Many of them go to a Institute for training themselves in this. But there are people who still try to study on their own. This post is for those people.
Every certification needs some hard work and concentration to complete them. You can study the entire syllabus and curriculum of CCNA in just five days. Yes, it is possible.
Here are the links given for each separate day. Download the files and start your self study right away.
CCNA Day 1
CCNA Day 2
CCNA Day 3
CCNA Day 4
CCNA Day 5
Note : These are no replacement for your Study Materials or Books or Videos or Simulators or Dumps or Training. These are just used to support your study for CCNA.
Tuesday, July 7, 2009
Self Study CCNA in 5 Days
Tuesday, May 12, 2009
Computer Abbreviations
Here is the list of Computer Abbreviations especially for Newbies and Computer Enthusiasts. It is always good to know them all
--- A ---
ADSL - Asymmetric Digital Subscriber Line
AGP - Accelerated Graphics Port
ALI - Acer Labs, Incorporated
ALU - Arithmetic Logic Unit
AMD - Advanced Micro Devices
APC - American Power Conversion
ASCII - American Standard Code for Information Interchange
ASIC - Application Specific Integrated Circuit
ASPI - Advanced SCSI Programming Interface
AT - Advanced Technology
ATI - ATI Technologies Inc.
ATX - Advanced Technology Extended
--- B ---
BFG - BFG Technologies
BIOS - Basic Input Output System
BNC - Barrel Nut Connector
--- C ---
CAS - Column Address Signal
CD - Compact Disk
CDR - Compact Disk Recorder
CDRW - Compact Disk Re-Writer
CD-ROM - Compact Disk - Read Only Memory
CFM - Cubic Feet per Minute
CMOS - Complementary Metal Oxide Semiconductor
CPU - Central Processing Unit
CTX - CTX Technology Corporation (Commited to Excellence)
--- D ---
DDR - Double Data Rate
DDR-SDRAM - Double Data Rate - Synchronous Dynamic Random Access Memory
DFI - DFI Inc. (Design for Innovation)
DIMM - Dual Inline Memory Module
DRAM - Dynamic Random Access Memory
DPI - Dots Per Inch
DSL - See ASDL
DVD - Digital Versatile Disc
DVD-RAM - Digital Versatile Disk - Random Access Memory
--- E ---
ECC - Error Correction Code
ECS - Elitegroup Computer Systems
EDO - Extended Data Out
EEPROM - Electrically Erasable Programmable Read-Only Memory
EPROM - Erasable Programmable Read-Only Memory
EVGA - EVGA Corporation
--- F ---
FC-PGA - Flip Chip Pin Grid Array
FDC - Floppy Disk Controller
FDD - Floppy Disk Drive
FPS - Frame Per Second
FPU - Floating Point Unit
FSAA - Full Screen Anti-Aliasing
FS - For Sale
FSB - Front Side Bus
--- G ---
GB - Gigabytes
GBps - Gigabytes per second or Gigabits per second
GDI - Graphical Device Interface
GHz - GigaHertz
--- H ---
HDD - Hard Disk Drive
HIS - Hightech Information System Limited
HP - Hewlett-Packard Development Company
HSF - Heatsink-Fan
--- I ---
IBM - International Business Machines Corporation
IC - Integrated Circuit
IDE - Integrated Drive Electronics
IFS- Item for Sale
IRQ - Interrupt Request
ISA - Industry Standard Architecture
ISO - International Standards Organization
--- J ---
JBL - JBL (Jame B. Lansing) Speakers
JVC - JVC Company of America
- K ---
Kbps - Kilobits Per Second
KBps - KiloBytes per second
--- L ---
LG - LG Electronics
LAN - Local Area Network
LCD - Liquid Crystal Display
LDT - Lightning Data Transport
LED - Light Emitting Diode
--- M ---
MAC - Media Access Control
MB - MotherBoard or Megabyte
MBps - Megabytes Per Second
Mbps - Megabits Per Second or Megabits Per Second
MHz - MegaHertz
MIPS - Million Instructions Per Second
MMX - Multi-Media Extensions
MSI - Micro Star International
--- N ---
NAS - Network Attached Storage
NAT - Network Address Translation
NEC - NEC Corporation
NIC - Network Interface Card
--- O ---
OC - Overclock (Over Clock)
OCZ - OCZ Technology
OEM - Original Equipment Manufacturer
--- P ---
PC - Personal Computer
PCB - Printed Circuit Board
PCI - Peripheral Component Interconnect
PDA - Personal Digital Assistant
PCMCIA - Peripheral Component Microchannel Interconnect Architecture
PGA - Professional Graphics Array
PLD - Programmable Logic Device
PM - Private Message / Private Messaging
PnP - Plug 'n Play
PNY - PNY Technology
POST - Power On Self Test
PPPoA - Point-to-Point Protocol over ATM
PPPoE - Point-to-Point Protocol over Ethernet
PQI - PQI Corporation
PSU - Power Supply Unit
--- R ---
RAID - Redundant Array of Inexpensive Disks
RAM - Random Access Memory
RAMDAC - Random Access Memory Digital Analog Convertor
RDRAM - Rambus Dynamic Random Access Memory
ROM - Read Only Memory
RPM - Revolutions Per Minute
--- S ---
SASID - Self-scanned Amorphous Silicon Integrated Display
SCA - SCSI Configured Automatically
SCSI - Small Computer System Interface
SDRAM - Synchronous Dynamic Random Access Memory
SECC - Single Edge Contact Connector
SODIMM - Small Outline Dual Inline Memory Module
SPARC - Scalable Processor ArChitecture
SOHO - Small Office Home Office
SRAM - Static Random Access Memory
SSE - Streaming SIMD Extensions
SVGA - Super Video Graphics Array
S/PDIF - Sony/Philips Digital Interface
--- T ---
TB - Terabytes
TBps - Terabytes per second
Tbps - Terabits per second
TDK - TDK Electronics
TEC - Thermoelectric Cooler
TPC - TipidPC
TWAIN - Technology Without An Important Name
--- U ---
UART - Universal Asynchronous Receiver/Transmitter
USB - Universal seri@l Bus
UTP - Unshieled Twisted Pair
--- V ---
VCD - Video CD
VPN - Virtual Private Network
--- W ---
WAN - Wide Area Network
WTB - Want to Buy
WYSIWYG - What You See Is What You Get
--- X ---
XGA - Extended Graphics Array
XFX - XFX Graphics, a Division of Pine
XMS - Extended Memory Specification
XT - Extended Technology
How to remove Dont Send Error Report?
Got fed up on receiving the Send/Dont Send Error Report????
Dont worry it is a easy task to disable this feature
Go to Control Panel--->Performance and Maintenance--->System--->Advanced Tab--->
Click on Error Reporting button-->Select Disable Error Reporting and Click OK
If some of you do not have the Performance and Maintenance Option in the Control Panel, then go to the System Properties and there click the Advanced Tab and then click on Error Reporting button to disable the feature. To open the System properties right click the My Computer and click Properties or double click System option present in the Control Panel.
Your are done!!!!
Now you are free from the error reporting.
Friday, March 20, 2009
All Run Commands in Windows XP
Ever felt lazy on searching for an application to open and work on it. Well if so then you can use the following run commands in your Run dialog box and then open the application as soon as possible.
You can access all these programs by going through START/RUN.
SQL Client Configuration - cliconfg
System Configuration Editor - sysedit
System Configuration Utility - msconfig
System File Checker Utility (Scan Immediately)- sfc /scannow
System File Checker Utility (Scan Once At Next Boot)- sfc /scanonce
System File Checker Utility (Scan On Every Boot) - sfc /scanboot
System File Checker Utility (Return to Default Setting)- sfc /revert
System File Checker Utility (Purge File Cache)- sfc /purgecache
System File Checker Utility (Set Cache Size to size x)-sfc/cachesize=x
System Information - msinfo32.
Task Manager – taskmgr
System Properties - sysdm.cpl
Task Manager – taskmgr
TCP Tester - tcptest
Telnet Client - telnet
Tweak UI (if installed) - tweakui
User Account Management- nusrmgr.cpl
Utility Manager - utilman
Windows Address Book - wab
Windows Address Book Import Utility - wabmig
Windows Backup Utility (if installed)- ntbackup
Windows Explorer - explorer
Windows Firewall- firewall.cpl
Windows Magnifier- magnify
Windows Management Infrastructure - wmimgmt.msc
Windows Media Player - wmplayer
Windows Messenger - msmsgs
Windows Picture Import Wizard (need camera connected)- wiaacmgr
Windows System Security Tool – syskey
Windows Update Launches - wupdmgr
Windows Version (to show which version of windows)- winver
Windows XP Tour Wizard - tourstart
Wordpad - write
Password Properties - password.cpl
Performance Monitor - perfmon.msc
Phone and Modem Options - telephon.cpl
Phone Dialer - dialer
Pinball Game - pinball
Power Configuration - powercfg.cpl
Printers and Faxes - control printers
Printers Folder – printers
Private Character Editor - eudcedit
Quicktime (If Installed)- QuickTime.cpl
Real Player (if installed)- realplay
Regional Settings - intl.cpl
Registry Editor - regedit
Registry Editor - regedit32
Remote Access Phonebook - rasphone
Remote Desktop - mstsc
Removable Storage - ntmsmgr.msc
Removable Storage Operator Requests - ntmsoprq.msc
Resultant Set of Policy (XP Prof) - rsop.msc
Scanners and Cameras - sticpl.cpl
Scheduled Tasks - control schedtasks
Security Center - wscui.cpl
Services - services.msc
Shared Folders - fsmgmt.msc
Shuts Down Windows - shutdown
Sounds and Audio - mmsys.cpl
Spider Solitare Card Game - spider
Malicious Software Removal Tool - mrt
Microsoft Access (if installed) - access.cpl
Microsoft Chat - winchat
Microsoft Excel (if installed) - excel
Microsoft Frontpage (if installed)- frontpg
Microsoft Movie Maker - moviemk
Microsoft Paint - mspaint
Microsoft Powerpoint (if installed)- powerpnt
Microsoft Word (if installed)- winword
Microsoft Syncronization Tool - mobsync
Minesweeper Game - winmine
Mouse Properties - control mouse
Mouse Properties - main.cpl
Nero (if installed)- nero
Netmeeting - conf
Network Connections - control netconnections
Network Connections - ncpa.cpl
Network Setup Wizard - netsetup.cpl
Notepad - notepad
Nview Desktop Manager (If Installed)- nvtuicpl.cpl
Object Packager - packager
ODBC Data Source Administrator- odbccp32.cpl
On Screen Keyboard - osk
Opens AC3 Filter (If Installed) - ac3filter.cpl
Outlook Express - msimn
Paint – pbrush
Keyboard Properties - control keyboard
IP Configuration (Display Connection Configuration) - ipconfi/all
IP Configuration (Display DNS Cache Contents)- ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents)- ipconfig /flushdns
IP Configuration (Release All Connections)- ipconfig /release
IP Configuration (Renew All Connections)- ipconfig /renew
IP Configuration(RefreshesDHCP&Re-RegistersDNS)-ipconfig/registerdns
IP Configuration (Display DHCP Class ID)- ipconfig/showclassid
IP Configuration (Modifies DHCP Class ID)- ipconfig /setclassid
Java Control Panel (If Installed)- jpicpl32.cpl
Java Control Panel (If Installed)- javaws
Local Security Settings - secpol.msc
Local Users and Groups - lusrmgr.msc
Logs You Out Of Windows - logoff.....
Accessibility Controls - access.cpl
Accessibility Wizard - accwiz
Add Hardware - Wizardhdwwiz.cpl
Add/Remove Programs - appwiz.cpl
Administrative Tools control - admintools
Adobe Acrobat (if installed) - acrobat
Adobe Designer (if installed)- acrodist
Adobe Distiller (if installed)- acrodist
Adobe ImageReady (if installed)- imageready
Adobe Photoshop (if installed)- photoshop
Automatic Updates - wuaucpl.cpl
Bluetooth Transfer Wizard – fsquirt
Calculator - calc
Certificate Manager - certmgr.msc
Character Map - charmap
Check Disk Utility - chkdsk
Clipboard Viewer - clipbrd
Command Prompt - cmd
Component Services - dcomcnfg
Computer Management - compmgmt.msc
Control Panel - control
Date and Time Properties - timedate.cpl
DDE Shares - ddeshare
Device Manager - devmgmt.msc
Direct X Control Panel (If Installed)- directx.cpl
Direct X Troubleshooter- dxdiag
Disk Cleanup Utility- cleanmgr
Disk Defragment- dfrg.msc
Disk Management- diskmgmt.msc
Disk Partition Manager- diskpart
Display Properties- control desktop
Display Properties- desk.cpl
Display Properties (w/Appearance Tab Preselected)- control color
Dr. Watson System Troubleshooting Utility- drwtsn32
Driver Verifier Utility- verifier
Event Viewer- eventvwr.msc
Files and Settings Transfer Tool- migwiz
File Signature Verification Tool- sigverif
Findfast- findfast.cpl
Firefox (if installed)- firefox
Folders Properties- control folders
Fonts- control fonts
Fonts Folder- fonts
Free Cell Card Game- freecell
Game Controllers- joy.cpl
Group Policy Editor (XP Prof)- gpedit.msc
Hearts Card Game- mshearts
Help and Support- helpctr
HyperTerminal- hypertrm
Iexpress Wizard- iexpress
Indexing Service- ciadv.msc
Internet Connection Wizard- icwconn1
Internet Explorer- iexplore
Internet Setup Wizard- inetwiz
Internet Properties- inetcpl.cpl
Remove Brontok Virus Manually
Here we will see on how to remove the most sticky virus "BRONTOK". Nowadays this is the virus that is found in most of the systems. It makes the Registry Editor (Regedit) disabled, it disables the Hidden folders and files option and it also sometimes disables the Task Manager.
The process for removing the brontok virus is simpler and without relying on any anti-virus softwares, we can remove the virus manually.
The procedure to do so :
1. Open the computer using Safe Mode with Command prompt and give the following two commands
reg delete HKCU\software\microsoft\windows\currentversion\policies\system /v "DisableRegistryTools"
run HKLM\software\microsoft\windows\currentversion\policies\system /v "DisableRegistryTools"
Now these two commands makes your registry editor enabled using which we will finish up the task.
2. Now go to Run and type regedit and hit enter.
3.Now follow the path
HKLM\Software\Microsoft\Windows\Currentversion\Run
and delete the entries in the right side of the screen having keywords "Brontok" or "Tok".
Now the virus is deleted but we have to make the folder options enabled.
4. Restart the system, open the registry editor and follow the path
HKCU\Software\Microsoft\Windows\Currentversion\Policies\Explorer\ 'NoFolderOption'
and delete this entry.
To be on the safe side search your computer with the name *.exe and do remember to include the hidden files option and delete the search results which has as a Folder Icon.
Now your system is free from Brontok Virus.
Thursday, March 19, 2009
Trace International Mobile Numbers - Worldwide
We have already seen on how to trace the mobile numbers in India.
There was a big thought by the users on how the database was maintained for such a large country like India. Still the question is unanswered.But as the users were gazed, more tricks came.
I saw this website which was capable of tracing mobilenumbers worldwide. This website is used for resolving any telephone number to its geographical location. Be it any country, any state and any city. It is possible to trace the mobile number from where it was originated and it also displays the Operator of the number.
Click on the following link to trace the numbers
Trace the Mobile Numbers - International
Disclaimer : Sharing the precise name and address details of mobile number is crime . It is against the privacy law. Land lines are more associated to houses or organizations, where as Mobile is very personal. The purpose of this tool is to give you some directions of location of mobile, so that if you call the person, you know how you'll be billed. Or you could recall the person by knowing the state and operator.
Monday, March 2, 2009
Find Invisible People in Gtalk, Yahoo Messenger
This is one of the most common trick which you would find in the Internet. But the trick wasn't available for Gtalk(Google Talk) for a long time. And soon after it was released too not many people knew the method to find out their friends who are invisible in the Chat list.
Well, the methods are pretty simple and they can be done by anyone .
GTalk (Google Talk)
1. Open the Chat window of the particular User on whom you want to find whether he/she is invisible.
2. Now Click on Option and Select the 'Go off the Record' option.
3. Now type some message and send it.
4. Now here is the trick, if you get a response "User is Offline and can't receive messages" in red font colour, then it means your victim is really offline.
5. If you dont get a response, it means your friend is in invisible mode and you are now ready to disturb them.
Yahoo Messenger
Well it is really easy to find out the same in Yahoo Messenger.
1. Open the Chat window of the particular User on whom you want to find whether he/she is invisible.
2. Now load the IMvironment "Doodle" and please wait since the IMvironment takes some time to load which depends on you connection speed.
3. Now if the Imvironemnt loads then the user is online.
These are tricks for checking the invisible people in Gtalk and Yahoo Messenger.
Sunday, March 1, 2009
Certifications
In the current situation where the recession plays an important role, the job market has found his dark shadow and for the freshers it is a night mare to enter the corporate IT World. So what are the other options available to them????
Well they have to update themselves with the upcoming technology and platforms and the factor which tells that they are in form is the Certifications.
Certifications play an important role in each and every body's profile. Say you are certified in something it means you have gone through the platform earlier and you are familiar with it and thus it reduces the company's training expenditure and you have a additional chance of getting recruited.
There are enormous amount of Certifications available for the aspirants and they can specialize them in which domain they need to be. And there are World Class Vendors which provides the Certifications. The Certifications not only helps you to fetch up a job but it also enhances your knowledge and your career options.
Some of the vendors are Sun, Cisco, Microsft, HP, IBM etc.
We will be concentrating on Cisco and Microsoft.
The Certifications available from Microsoft are :
MCTS
Microsoft Certified Technology Specialist (MCTS) certifications enable professionals to target specific technologies and to distinguish themselves by demonstrating in-depth knowledge and expertise in Microsoft specialized technologies.
MCITP
Microsoft Certified IT Professional (MCITP) certifications demonstrate comprehensive skills in planning, deploying, supporting, maintaining, and optimizing IT infrastructures.
MCPD
Microsoft Certified Professional Developer (MCPD) certifications demonstrate comprehensive skills in designing, developing, and deploying applications for a particular job role. These certifications show that you have the skills required to perform the job successfully.
Microsoft Certified Architect Program
The Microsoft Certified Architect program recognizes and provides advanced certification to practicing architects in an enterprise setting.
Microsoft Certified Master Program
The Microsoft Certified Master program enables experienced IT professionals to demonstrate and validate their ability to successfully design and implement solutions that meet the most complex business requirements.
MCDST
A Microsoft Certified Desktop Support Technician (MCDST) demonstrates technical and customer service skills in troubleshooting hardware and software operation issues in Microsoft Windows environments.
MCLC
The Microsoft Certified Learning Consultant (MCLC) credential recognizes Microsoft Certified Trainers (MCTs) whose job roles have grown to include frequent consultative engagements with customers. These MCTs are experts in designing and delivering customized learning solutions.
MCSA
A Microsoft Certified Systems Administrator (MCSA) administers network and systems environments based on the Windows operating systems. Specializations include the MCSA: Messaging and the MCSA: Security.
MCSE
A Microsoft Certified Systems Engineer (MCSE) designs and implements an infrastructure solution that is based on the Windows operating system and Windows Server System software. Specializations include the MCSE: Messaging and the MCSE: Security.
MCDBA
A Microsoft Certified Database Administrator (MCDBA) designs, implements, and administers Microsoft SQL Server databases.
MCT
A Microsoft Certified Trainer (MCT) is a qualified instructor who is certified by Microsoft to deliver Microsoft training courses to IT professionals and developers.
MCAD
A Microsoft Certified Application Developer (MCAD) uses Microsoft technologies to develop and maintain department-level applications, components, Web or desktop clients, or back-end data services.
MCSD
A Microsoft Certified Solution Developer (MCSD) designs and develops leading-edge business solutions with Microsoft development tools, technologies, platforms, and the Windows operating system.
Microsoft Certified Business Solutions Specialist
A Microsoft Certified Business Management Solutions Specialist demonstrates proficiency with Microsoft Dynamics and related business products.
Microsoft Certified Business Management Solutions Professional
A Microsoft Certified Business Management Solutions Professional demonstrates professional proficiency with Microsoft Dynamics in one of three knowledge areas: applications, developer, or installation and configuration.
MOS
A Microsoft Office Specialist (Office Specialist) is globally recognized for demonstrating advanced skills in using Microsoft desktop software.
MCAS
A Microsoft Certified Application Specialist (MCAS) has advanced business skills with the 2007 Microsoft Office system and Windows Vista.
CISCO
Now as far as Cisco is concerned there are 4 levels of certifications Entry, Associate, Professional and Expert with seven different paths.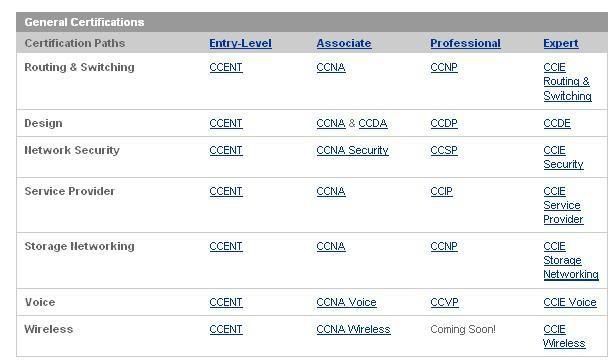
And similarly there are a lot of vendors offering a lot of Certifications, we will see all of them as the time passes.
Tuesday, February 24, 2009
Google Search Engine
Google is world’s most popular and powerful search engine which has the ability to accept pre-defined commands as input and produce unbelievable results. This enables malicious users like hackers, crackers, and script kiddies etc to use Google search engine extensively to gather confidential or sensitive information which is not visible through common searches.
Google’s Advance Search Query Syntaxes
Below discussed are various Google’s special commands and I shall be explaining each command in brief and will show how it can be used for critical information digging.
[ intitle: ]
The “intitle:” syntax helps Google restrict the search results to pages containing that word in the title. For example, “intitle: Windows XP" (without quotes) will return links to those pages that has the word "Windows" in their title, and the word "XP" anywhere in the page.
Similarly, if one has to query for more than one word in the page title then in that case “allintitle:” can be used instead of “intitle” to get the list of pages containing all those words in its title. For example using “intitle: Windows intitle: XP” is same as querying “allintitle: Windows XP”.
[ inurl: ]
The “inurl:” syntax restricts the search results to those URLs containing the search keyword. For example: “inurl: edu” (without quotes) will return only links to those pages that have "edu" in the URL.
Similarly, if one has to query for more than one word in an URL then in that case “allinurl:” can be used instead of “inurl” to get the list of URLs containing all those search keywords in it. For example: “allinurl: forum/edu“ will look for the URLs containing “forum” and “edu"The slash (“/”) between the words will be ignored by Google.
[ site: ]
The “site:” syntax restricts Google to query for certain keywords in a particular site or domain. For example: “Windows site:google.com” (without quotes) will look for the keyword “Windows” in those pages present in all the links of the domain “google.com”. There should not be any space between “site:” and the “domain name”.
This can be used for searching on rapidshare as well.
[ filetype: ]
This “filetype:” syntax restricts Google search for files on internet with particular extensions (i.e. doc, pdf or ppt etc). For example: “filetype:doc site:gov confidential” (without quotes) will look for files with “.doc” extension in all government domains with “.gov” extension and containing the word “confidential” either in the pages or in the “.doc” file. i.e. the result will contain the links to all confidential word document files on the government sites.
[ link: ]
“link:” syntax will list down webpages that have links to the specified webpage. For Example: “link:google.com” will list webpages that have links pointing to the google homepage. Note there can be no space between the "link:" and the web page url.
[ related: ]
The “related:” will list web pages that are "similar" to a specified web page. For Example: “related:google.com” will list web pages that are similar to the google homepage. Note there can be no space between the "related:" and the web page url.
[ cache: ]
The query “cache:” will show the version of the web page that Google has in its cache. For Example: “cache:yahoo.com” will show Google's cache of the Google homepage. Note there can be no space between the "cache:" and the web page url.
If you include other words in the query, Google will highlight those words within the cached document. For Example: “cache:yahoo.com user” will show the cached content with the word "user" highlighted.
[ intext: ]
The “intext:” syntax searches for words in a particular website. It ignores links or URLs and page titles. For example: “intext:Windows” (without quotes) will return only links to those web pages that has the search keyword "Windows" in its webpage.
[ phonebook: ]
“phonebook” searches for U.S. street address and phone number information. For Example: “phonebook:Lisa+CA” will list down all names of person having “Lisa” in their names and located in “California (CA)”. This can be used as a great tool for hackers incase someone want to do dig personal information for social engineering.
The syntaxes will help you to have a better search result with Google. Try it and Enjoy searching in Google guys!!!
Note : Some of the syntaxes would not work since Google frequently does changes in the queries and syntaxes.
Trace Mobile Number
You would have seen how to trace a IP Address by seeing my other post,there are a lot of other sites similar to that to trace the IP address.
But have you ever thought that you would be able to trace the Mobile Number. Well if you still think is it possible??? The answer is a big YES
I came across the following website which would help you to track down the Mobile Number, this site will be able to tell you the operator and the region where the mobile was operated and the Signaling method i.e whether GSM or CDMA.
Click the below link :
TRACE THE NUMBER NOW
The following image describes it more 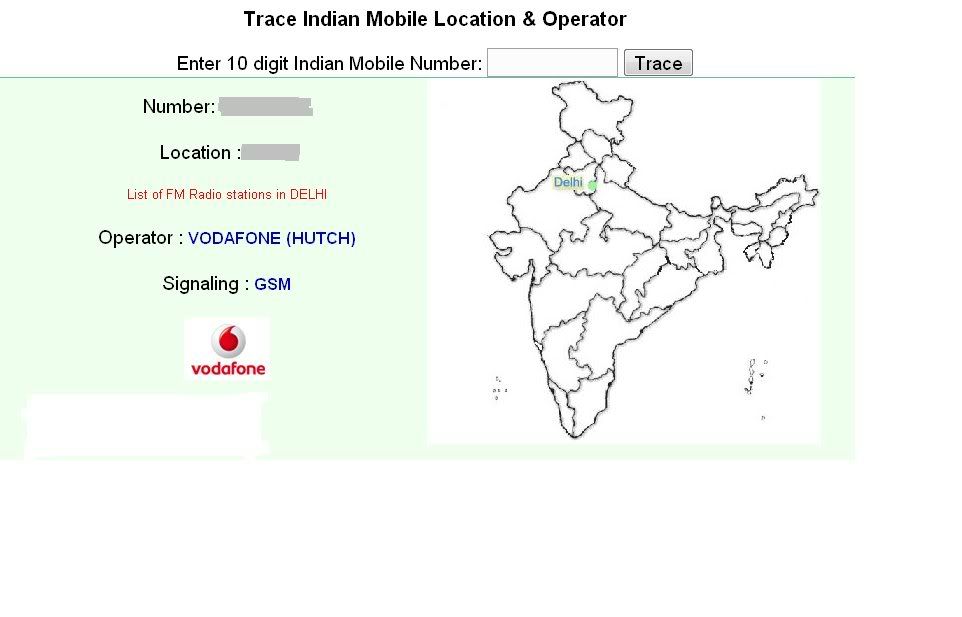
Sorry guys the tool works only for mobilenumbers in INDIA.
Disclaimer : Sharing the precise name and address details of mobile number is crime in India. It is against the privacy law. Land lines are more associated to houses or organizations, where as Mobile is very personal. The purpose of this tool is to give you some directions of location of mobile, so that if you call the person, you know how you'll be billed. Or you could recall the person by knowing the state and operator.
Windows Genuine Validation
Nowadays most people encounter the Windows Genuine Validation and the you get the software counterfeiting problem well the solution of the problem is very simple, we just need to edit the product id for the current Windows XP product.
Just follow the following steps and you can get rid of the problem
1. Open Notepad
2. Paste the following code and then save the file as with whatever name you want to but remember to name the file with the extension .reg, so your filename should be shown as WindowsGen.reg (example).
3. Now the next step is to merge the file, which is nothing but to double click the file.
4. A dialog box appears and asks you confirmation whether to join the file with the registry or not, just click OK and then again a dialog box appears and click OK.
5. You are done. Just refresh the desktop or restart the computer and you will find the Software counterfeiting sign disappeared.
Now your Windows is Genuine.
The Code is :
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion]
"CurrentBuild"="1.511.1 () (Obsolete data - do not use)"
"ProductId"="55274-640-1011873-23081"
"DigitalProductId"=hex:a4,00,00,00,03,00,00,00,35,35,32,37,34,2d,36,34,30,2d,\
31,30,31,31,38,37,33,2d,32,33,30,38,31,00,2e,00,00,00,41,32,32,2d,30,30,30,\
30,31,00,00,00,00,00,00,00,86,56,4e,4c,21,1b,2b,6a,a3,78,8e,8f,98,5c,00,00,\
00,00,00,00,dd,da,47,41,cc,6b,06,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,38,31,30,32,36,00,00,00,00,00,00,00,b5,16,\
00,00,83,83,1f,38,f8,01,00,00,f5,1c,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,66,e5,70,f3
"LicenseInfo"=hex:33,b7,21,c1,e5,e7,cd,4b,fd,7c,c6,35,51,fd,52,57,17,86,3e,18,\
d3,f4,8c,8e,35,32,7b,d1,43,8d,61,38,60,a4,ca,55,c9,9a,35,17,46,7a,4f,91,fc,\
4a,d9,db,64,5c,c4,e2,0f,34,f3,ea
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WPAEvents]
"OOBETimer"=hex:ff,d5,71,d6,8b,6a,8d,6f,d5,33,93,fd
Tuesday, February 17, 2009
IP Tracker
Ever thought of tracing the Location of a particular IP
Well its simple.Those days it was very difficult and we had to obtain some sort of licenses to track down the IP's.
But now it is very easy to obtain the exact location of the IP. You can get the exact Latitude and Longitude location of the person and the country and even the Internet Service Provider (ISP).
There are a lot of applications for the purpose. But i found this application could be much useful.
Its very simple, Just enter the IP address in the box provided and then hit Search button
|
And your own IP Information
Read More...
Remove Virus Manually Part-I
Do you suspect your computer for viruses in it????
Are there sudden changes in your Operating system or your computer???
Well there are various applications for scanning the viruses but you need to install a specific application i.e. a Antivirus to do the job but ever thought that any other application could do the same job.
Yup, there are ways, heard of the Winrar Application most of you would have. Just open the application and open the specific path where you have suspected of virus and then in the content window it shows the Hidden Virus and thats the job, just select them and delete them forever.
This particular method works fine Newfolder.exe and the Autorun.inf virus.
Try it guys!!
Tuesday, February 10, 2009
Configure a VPN Connection
How to configure a VPN
Guys I saw this article and thought this could be useful to everyone on how to create and manage a VPN connection. Try doing it guys!!!!!
If you are looking for a free and easy way to create a VPN(Virtual Private Network) connection to another computer, share files, remote control or share screens between computers? Gbridge helps you to manage your multiple PCs, and collaborate works with close friends. In addition, you will be able to use it when you want to privately exchange large media files with your friends. Gbridge is a free tool which you can use to sync folders, share files, control another computer, share your desktop, or chat. It connects two computers directly and securely.
Find the application at : http://www.gbridge.com/
Once you are done with the installation, you’ll be asked for your Google account information, and to give a host name in the login screen .
When everything’s set up, you’re ready to go, but you need two systems to create a VPN connection so set up a Gbridge on other computers you where you want to create a virtual network. You can install and auto-start Gbridge on multiple computers, using the same Gmail logon, and it will keep all those computers connected and ready to trade or stream files.
The easiest way to use Gbridge is to create SecureShares Hit the big button for SecureShares at the top on the Gbridge client that’s doing the sharing, choose a folder, and choose the people who can access it and set a password by clicking on Create SecureShare as show below.From here you would choose the people who can access it and set a password.
So if your friends want to quickly connect to your computer, just ask them to install the Gbridge client software and you can now send large files, instantly play MP3’s off each other’s computer, share your desktops, and even create photo slideshows from your folders and let others watch.
VPN (Virtual Private Network)
What is VPN?
A VPN network can send voice, data, and video over secure and encrypted private channels in the public network. There are many VPN client programs that are configure in such a way that all the IP traffic must pass the VPN tunnels before reaching the destination.
VPN Features
A VPN connection can provide the following features.
• Global Networking
• Broadband Network Compatibility System
• Secure Communication
• Cost Effective solution for the corporate offices.
• Reduced Operational cost
• Faster Return on investment
Still confused????
See tho other post on VPN on how to configure it between two systems and share data
Subscribe via email
Categories
- Antivirus (2)
- CCNA (1)
- Certifications (2)
- Cisco (1)
- Hacks (3)
- Networks (3)
- Tips and Tweaks (8)
- VPN (2)
- Windows (4)